Every time I use my Apple computers, it becomes more and more apparent that Steve Jobs has wholly sold out user’s privacy. Publicly Jobs denies privacy violations:
We’ve always had a very different view of privacy than some of our colleagues in the [Silicon] Valley. We take privacy extremely seriously…. A lot of people in the Valley think we’re really old-fashioned about this…Privacy means people know what they’re signing up for, in plain English and repeatedly…. let them know precisely what you’re going to do with their data. That’s what we think.
But use of an Apple computer on the ground suggests differently.
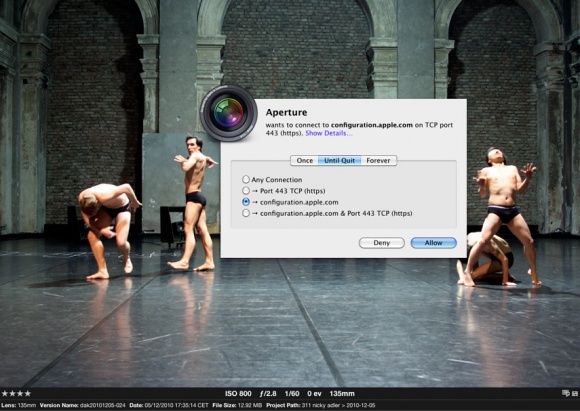
Apple Aperture violating your privacy
Let’s start with a simple example from a pro app: Apple’s Aperture goes after configuration.apple.com every time even with all web checkboxes turned off. l.google.com (location for Google) is understandable if you are using Aperture’s built-in geo location services. But not if you have it turned off as I do.
I’m not the first one to find Apple’s monitoring of our use of their apps disturbing. The issue of iLife ’06 phoning home was a sore spot as far back as 2006. What goes on with iPhones with individual apps tracking every use along with your unique iPhone ID and your Facebook profile is astonishing.
But with the pro apps for which we are paying hundreds of dollars, one would think that one had more than paid for the right to privacy.
Apparently not.
What is even more disturbing is that with a virgin Little Snitch install, almost all Apple servers and services are considered safe and permitted out of the box. Why does Objective Development implicitly trust Apple? Moreover, there is nothing to prevent Apple from engineering around Little Snitch and Apple has certainly done so.

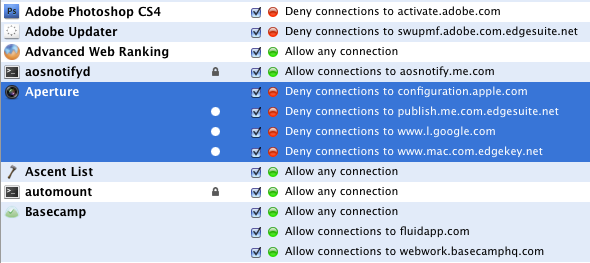
known Apple privacy violations in Aperture
I am slowly becoming convinced that there are back doors into even our fruity and once alternative Apple computers. I wonder if user tracking was a deal Apple signed with the devil to be given free road in telecommunications. For decades, Microsoft has taken the side of the US government and security institutions against users. There are hidden files on Windows computers which log all your internet visits and emails in plain text. Very handy for law enforcement. Here’s what one IT professional’s experience:
Internet history, documents and all sorts of potentially sensitive data is cached as well. When recovering documents for users I’ve found copies of those documents in some really strange places. The user was just glad I recovered some or all of their lost work. I just sat there scratching my head as to why there was a copy there and not in the normal temp dir where you’d think such files would be kept. Varies from version to version as to where those things turn up.
If this doesn’t worry you as a US citizen, take a closer look at the supervisory protection offered by your courts. No requests for wiretaps were turned down in 2009 out of 2,376. These are only the visible wiretaps and not the secret ones rubber stamped behind closed doors. That none were turned down suggests that US law enforcement is not being supervised by the courts. It’s the same as all students getting A+ on their exams.
The Obama administration is openly insisting on unrestricted access to all online communication. Governments all over the world and most notably the UK have enacted laws to force you to reveal the key to any encrypted data with penalties of up to two years in jail. In the case of the UK, even the assessment of taxes or any charge payable to a government department justifies invoking RIPA. The list of agencies who are allowed to invoke the act is forty or more and includes local councils including fire authorities and the Charity Commission.
There is perhaps nowhere where your data is less secure than the UK. Basically if you are travelling to Britain, you’d best take a laptop with next to no information on it: just the bare minimum to access your email. You are free to complain to the Investigatory Powers Tribunal about inappropriate use of surveillance authority under RIPA. In ten years, 956 complaints were registered: only 4 were upheld. Again, the case of all students receiving A+. Those grades don’t tally well with the five law enforcement officers jailed for running illegal surveillance networks using RIPA means to ill ends.
Glenn Greenwald quotes surveillance expert Julian Sanchez:
If you want to sift through communications in bulk, it’s only going to be feasible with a systemic backdoor.
Apple is doing their share in providing those backdoors and detailed tracking of its users. It does no harm that the data they are collecting on consumers gives them enormous power in the marketplace. So not only do they get favours from the powers to be, they make money to. Plutocratic oligarchy at its best.
What is Apple doing with all its loot? Spending it on filing more patents. The spurious patent strongbox of Apple is filled like a pirate’s chest.
Google is no better than Apple and probably worse. So as a computer user, you have three commercial choices of whom to trust with access to your data:
- Google, the greatest data miners in history and close allies of the US government
- Microsoft, proven collaborators (how much of their poor security practices are deliberate and how much is intentional is the only question)
- Apple who is slowly violating its core principles and tracking you for all its worth
No matter where you turn, you are compromised before you leave the gate, easily trackable at every moment online and with your cellphone. You are always in the matrix.
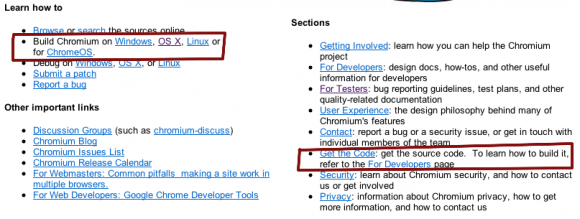
Google’s Chrome browser installs invasive tools by default that check in with Google on every run, ostensibly looking for updates. A more privacy aware open source version of Chrome called Chromium exists for Mac OS X in nightly builds no less. For some reason Google hides those builds on their Chromium public pages, only offering instructions on how to build the damn browser from scratch.

Google offers only Chromium build source
It’s looking more and more like Linux is our only option if we want to retain our privacy. I’m surprised to see Steve Jobs sell out like this. I suppose he’d call it pragmatism. I’d suggest it’s betrayal.
If I decide to stop using Apple computers, that’s 5 personal computers down and ten more company computers. I think it’s time someone took the bull by the horns and started producing sanitisers for of OS X which shut down all of this phoning home with a combination of Little Snitch behaviour and automated creation of hosts files, with regular monitoring and testing of other backdoors. The task is very onerous as Apple can always enclose special keys or particular data in encrypted files. The only way to prevent your computer being compromised is to allow no outgoing communication at all without your assent and a minimum at that.
Particularly vulnerable is Mobile Me. With Mobile Me, you are able to share Mail, Contacts, Calendar and control your computer remotely depending on what options you enable. Presumably Mobile Me communicates all of the requisite information, whether you turn on selected services or not. So once you’ve used Mobile Me even once, US authorities have full access to all of your computers.
I had to help my own sister with her Mac. The only system which worked reliably to access her Mac and help her with it was Mobile Me. Mobile Me was a blessing to be able to get her new Macbook Pro working just right. On the other hand, signing up and enabling some of its features on my own computers probably compromised decades of relatively secure computing practices.
One of the reasons that Microsoft got away from its antitrust case after an initial guilty verdict are their ties with national security in the US. The cost to national security by breaking down the computer OS monopoly were considered larger than the gain by enforcing anti-monopoly and antitrust legislation. The backdoors and collaboration with national security were Microsoft’s get-out-of-jail card. Google plays the same card and thus can break privacy and copyright laws with relative impunity.
Steve Jobs is no fool. Having seen competitor one thrive and survive via collaboration (Microsoft) and seen competitor two burst from zero to exceed Apple’s market capitalisation earned over decades in just a few short years (Google) via such collaboration, there’s just no way the gentleman feels in a position to protect users.
On the other hand, Apple users are said to be wealthier and better educated than Windows users. Surely one day we’ll be smart enough to realise we’ve been had and we are all sailing in boats with sieve ridden hulls.
Ironically, these backdoors can help to protect the innocent. In one case, the surveillance backdoors on the iPhone saved an innocent man from 5 consecutive sentences of 14 years on false rape charges. But the exception proves the rule. We are under more and more tacit surveillance using our Apple phones and computers.
What could Apple do to reengender trust among its users? Remove any calls to its servers without explicit authorisation from the OS or their own applications. For those who want a simpler experience, give them a global security setting which means something. Something like three simple options:
- No calls home without specific authorisation (i.e. manually checking for version and software updates).
- Anonymous information for updates without system profiles and for time with no location information.
- Full functionality for the best and simplest Apple experience.
Unfortunately I don’t think it’s going to happen.
Sooner or later if you value your privacy, a permanent exile in the Antarctic icecap with the other penguins looms. For political activists, Linux should be de rigeur as the starting OS. It’s a little difficult for me at this point with decades now invested in expertise and productivity on Apple computers. I own and use dozens of great OS X only shareware programs as well as commercial graphics and video applications like Aperture, Photoshop and Final Cut Pro for which there are no adequate equivalents at the South Pole.
It’s looking like a second computer is in line now for just private writing and private life. Even if you can’t leave behind Microsoft, Google and Apple for your business life, you should get a second machine Linux machine which never goes online. Even an Apple computer would be fine, as long as you never ever plug it in. The recommendation is epoxy for the networking ports which include Ethernet and Firewire and removal of wireless functionality. DHCP is just too easy and tempting. You’ll need to hold on to USB for backups.

Alec Kinnear
Alec has been helping businesses succeed online since 2000. Alec is an SEM expert with a background in advertising, as a former Head of Television for Grey Moscow and Senior Television Producer for Bates, Saatchi and Saatchi Russia.
More on Aperture’s behavior and how Apple could make us feel better:
blog.jonalper.com/2010/aperture-places-privacy/
I think it’s very premature to say Apple is doing something malicious without knowing the contents of that communication.
Hi emory,
Just communicating with home base without my permission is already borderline malicious.
That’s the point. We don’t know what is in the communication. Most people don’t even know that the communication is there. I never agreed to such communication. If it’s stuck in the ELUA deep in the fine print, that’s not good enough. Frankly I don’t want to do business with a computer company which is communicating with home base without my permission.
If Apple has changed their policy, and apparently they have, many of us are now in a difficult position as when we made our huge investment in Apple technology, Apple didn’t tell us we’d face this kind of invasion of privacy in the future. Quite the contrary.
emory is correct. Saying that apple is stealing your info is complete BS. While they might be doing just that, saying you see software connect to a server is hardly proof. There are a vast number of valid reasons to contact servers. Communicating with icloud, tweeking and editing code to keep everything running smooth. Your computer sends out so many communications just for e-mail that are so complex and difficult to understand people spend there entire undergraduate careers in computer science understanding and the next 4 year of a phd program to master it. This is not trivial stuff. If you dont want to comunicate with the home base you have to disconnect the internet. Or get a degree in computer science or equivalent and hack the hell out of your computer.
Hi Frank,
Apple and their partners are stealing your information. If you’ve signed up for iCloud then you’ve accepted sharing your information with Apple.
I haven’t.
It’s not that difficult to understand. Just install Little Snitch to watch it happen.
A lot can be circumvented in hosts as well.
Apple made certain promises regarding respecting our privacy, promises they’ve slowly been reneging on over the last five years.
Based on Apple’s dishonesty, it’s time to stop buying Apple computers.
Little Snitch is only telling you that an outbound connection is occurring. It doesn’t tell you what that is.
If you wanted to see what it was, you could, but then you would disprove your own salacious hypothesis.
Emory if you don’t realize that the new Apple is data mining by now, your naivete is astonishing.
Remind me to play poker with you some time.
I actually looked into this. I agree with the other posters. Using wireshark/tcpdump and lsof you can see what is happening when it makes that connection.
There is nothing malicious about the communication, it’s fetching a plist to ensure it has the right values for network services.
Hi slapulation,
Thanks for checking a single communication from Apple. The real question is how easily can all these “benevolent” checks be turned into something more aggressive.
I would guess quite easily. The more of them there are, the more open your computer is in case an external party wants access.
Apple’s OS is Swiss Cheese now in terms of unlocked doors to external servers.
Something more aggressive like what, the tracking cookies and counters you are collecting on everyone visiting this website?
You’re collecting more data about visitors to your website than Apple is collecting about users of Aperture; you could easily start collecting even more information and inserting browser exploits into your webpage to install malicious software that monitors every visitor.
I know it doesn’t feel good to be wrong, but you make some pretty serious accusations for somebody with zero evidence.
Yes, we are keeping track of how people found our site.
But it’s not going through third party collection agencies so it’s relatively harmless. Not tied to anything else related to you: your Facebook, your Google account, any of your other purchases.
Unlike Apple.
Thanks for helping make my point.
Insulting and pointless comment from an airhead deleted. Better luck next time.
Ad hominem attacks are not accepted, nor does Apple bootlicking endear you either.
Er,
Since this was written, it’s a slam dunk that Apple are spying on you; it was all over the media. Why are people so niave?
Because this isn’t how they “spy” on you. This is how the software checks for updates. Derp.
Forget about privacy, its an illusion, no matter what platform you are using…
Even if you cut the internet:
Spy have used those method for 30 years!
If you want true privacy move to Antarctica and wear a foil hat, and DO NOT USE ELECTRONIC DEVICE.
Even then, they are working on way to read your brain from satellite!